New updated leads4pass NSE6_FML-6.2 Dumps with PDF file and VCE practice exam engine to help pass the Fortinet NSE 6 – FortiMail 6.2 Exam successfully!
leads4pass NSE6_FML-6.2 exam dumps contain 30 exam questions and answers, covering complete Fortinet NSE 6 – FortiMail 6.2 certification exam questions, and verified to be true and valid, check here to get the latest leads4pass NSE6_FML-6.2 dumps: https://www.leads4pass.com/nse6_fml-6-2.html (PDF+VCE).
Check out the NSE6_FML-6.2 PDF exam questions and answers shared for free: https://drive.google.com/file/d/1Ecm78T18OsOnYQ5GLudk8N74BgqZzBp-/
Also, read the latest 15 leads4pass NSE6_FML-6.2 exam questions and answers online:
Question 1:
Refer to the exhibit.

Which statement describes the pre-registered status of the IBE user extuser2@external.lab?
A. The user has received an IBE notification email, but has not accessed the HTTPS URL or attachment yet.
B. The user account has been de-activated, and the user must register again the next time they receive an IBE email.
C. The user was registered by an administrator in anticipation of IBE participation.
D. The user has completed the IBE registration process, but has not yet accessed their IBE email.
Correct Answer: D
Reference: https://docs.fortinet.com/document/fortimail/6.4.2/administration-guide/470401/configuring-ibe-users
Question 2:
FortiMail is configured with the protected domain example.com.
Which two envelope addresses will require an access receive rule, to relay for unauthenticated senders? (Choose two.)
A. MAIL FROM: accounts@example.com RCPT TO: sales@external.org
B. MAIL FROM: support@example.com RCPT TO: marketing@example.com
C. MAIL FROM: training@external.org RCPT TO: students@external.org
D. MAIL FROM: mis@hosted.net RCPT TO: noc@example.com
Correct Answer: BD
Question 3:
What three configuration steps are required to enable DKIM signing for outbound messages on FortiMail? (Choose three.)
A. Generate a public/private key pair in the protected domain configuration
B. Enable DKIM check in a matching session profile
C. Enable DKIM check in a matching antispam profile
D. Publish the public key as a TXT record in a public DNS server
E. Enable DKIM signing for outgoing messages in a matching session profile
Correct Answer: ABD
Question 4:
Which three statements about SMTPS and SMTP over TLS are true? (Choose three.)
A. SMTP over TLS connections are entirely encrypted and initiated on port 465
B. SMTPS encrypts the identities of both the sender and receiver
C. The STARTTLS command is used to initiate SMTP over TLS
D. SMTPS encrypts only the body of the email message
E. SMTPS connections are initiated on port 465
Correct Answer: BCE
Question 5:
Refer to the exhibit.

Which two statements about the MTAs of the domain example.com are true? (Choose two.)
A. The external MTAs will send email to mx.example.com only if mx.hosted.com is unreachable
B. The PriNS server should receive all email for the example.com domain
C. The primary MTA for the example.com domain is mx.hosted.com
D. The higher preference value is used to load balance more email to the mx.example.com MTA
Correct Answer: AC
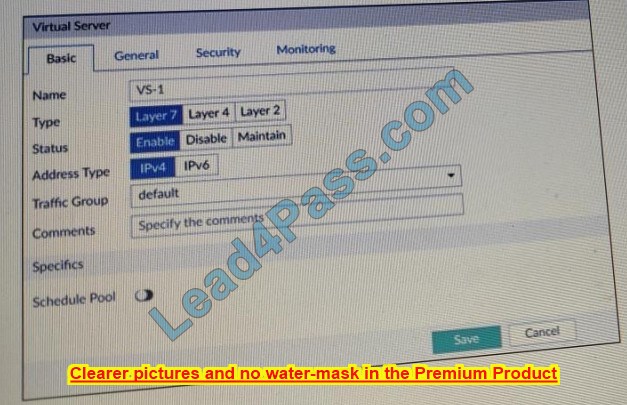
Question 6:
Refer to the exhibit.

Which two statements about the access receive rule are true? (Choose two.)
A. Email matching this rule will be relayed
B. Email must originate from an example.com email address to match this rule
C. Senders must be authenticated to match this rule
D. Email from any host in the 10.0.1.0/24 subnet can match this rule
Correct Answer: AB
Question 7:
Refer to the exhibit.

Which statement describes the impact of setting the User inactivity expiry time option to 90 days?
A. IBE user accounts will expire after 90 days of inactivity and must register again to access a new IBE email message
B. Registered IBE users have 90 days from the time they receive a notification email message to access their IBE email
C. After initial registration, IBE users can access the secure portal without authenticating again for 90 days
D. First-time IBE users must register to access their email within 90 days of receiving the notification email message
Correct Answer: A
Question 8:
Refer to the exhibit.

It is recommended that you configure which three access receive settings to allow outbound email from the example.com domain on FML-1. (Choose three.)
A. The Sender pattern should be set to *@example.com
B. The Action should be set to Relay
C. The Recipient pattern should be set to 10.29.1.45/24
D. The Enable check box should be cleared
E. The Sender IP/netmask should be set to 10.29.1.45/32
Correct Answer: BDE
Question 9:
Refer to the exhibit.

Which message size limit will FortiMail apply to the outbound email?
A. 204800
B. 1024
C. 51200
D. 10240
Correct Answer: A
Question 10:
A FortiMail administrator is investigating a sudden increase in DSNs being delivered to the protected domain for undeliverable email messages.
After searching the logs, the administrator identifies that the DSNs were not generated as a result of any outbound email sent from the protected domain.
Which FortiMail antispam technique can the administrator use to prevent this scenario?
A. Spam outbreak protection
B. Bounce address tag validation
C. Spoofed header detection
D. FortiGuard IP Reputation
Correct Answer: A
Question 11:
While reviewing logs, an administrator discovers that an incoming email was processed using policy IDs 0:4:9.
Which two scenarios will generate this policy ID? (Choose two.)
A. Email was processed using IP policy ID 4
B. Incoming recipient policy ID 9 has the exclusive flag set
C. FortiMail applies the default behavior for relaying inbound email
D. FortiMail configuration is missing an access delivery rule
Correct Answer: CD
Question 12:
Refer to the exhibit.

Which two message types will trigger this DLP scan rule? (Choose two.)
A. An email message with a subject that contains the term “credit card” will trigger this scan rule
B. An email that contains credit card numbers in the body, attachment, and subject will trigger this scan rule
C. An email message that contains credit card numbers in the body will trigger this scan rule
D. An email sent from sales@internal.lab will trigger this scan rule, even without matching any conditions
Correct Answer: BC
Question 13:
Refer to the exhibit.

An administrator has enabled the sender reputation feature in the Example_Session profile on FML-1. After a few hours, the deferred queue on the mail server starts filling up with undeliverable emails.
What two changes must the administrator make to fix this issue? (Choose two.)
A. Apply a session profile with sender reputation disabled on a separate IP policy for outbound sessions
B. Clear the sender reputation database using the CLI
C. Create an outbound recipient policy to bypass outbound email from session profile inspections
D. Disable the exclusive flag in IP policy ID 1
Correct Answer: AD
Question 14:
Refer to the exhibit.

The exhibit shows a FortiMail active-passive setup.
Which three actions are recommended when configuring the primary FortiMail HA interface? (Choose three.)
A. Disable Enable port monitor
B. In the Heartbeat status drop-down list, select Primary
C. In the Peer IP address field, type 172.16.32.57
D. In the Virtual IP action drop-down list, select Use
E. In the Virtual IP address field, type 172.16.32.55/24
Correct Answer: ABD
Question 15:
Which two CLI commands, if executed, will erase all data on the log disk partition? (Choose two.)
A. execute formatmaildisk
B. execute formatmaildisk_backup
C. execute formatlogdisk
D. execute partitionlogdisk 40
Correct Answer: CD
Reference: https://docs.fortinet.com/document/fortimail/6.2.0/cli-reference/588825/formatlogdisk
…
Latest Complete 30 NSE6_FML-6.2 Certification Exam Questions With Answers Get leads4pass NSE6_FML-6.2 Exam Dumps: https://www.leads4pass.com/nse6_fml-6-2.html (PDF+VCE)