New updated leads4pass NSE7_OTS-6.4 Dumps with PDF file and VCE practice exam engine to help pass the Fortinet NSE 7 – OT Security 6.4 Exam successfully!
leads4pass NSE7_OTS-6.4 exam dumps contain 35 exam questions and answers, covering complete Fortinet NSE 7 – OT Security 6.4 certification exam questions, and verified to be true and valid, check here to get the latest leads4pass NSE7_OTS-6.4 dumps: https://www.leads4pass.com/nse7_ots-6-4.html (PDF+VCE).
Check out the NSE7_OTS-6.4 PDF exam questions and answers shared for free: https://drive.google.com/file/d/1rP_jaCQIoV_acgQGul7EJxR4-0NCjVhW/
Also, read the latest 15 leads4pass NSE7_OTS-6.4 exam questions and answers online:
Question 1:
Which three criteria can a FortiGate device use to look for a matching firewall policy to process traffic? (Choose three.)
A. Services defined in the firewall policy.
B. Source defined as internet services in the firewall policy
C. Lowest to highest policy ID number
D. Destination defined as internet services in the firewall policy
E. Highest to lowest priority defined in the firewall policy
Correct Answer: ABD
Question 2:
Refer to the exhibit and analyze the output.

Which statement about the output is true?
A. This is a sample of a FortiAnalyzer system interface event log.
B. This is a sample of an SNMP temperature control event log.
C. This is a sample of a PAM event type.
D. This is a sample of FortiGate interface statistics.
Correct Answer: A
Question 3:
Which three Fortinet products can be used for device identification in an OT industrial control system (ICS)? (Choose three.)
A. FortiNAC
B. FortiManager
C. FortiAnalyzer
D. FortiSIEM
E. FortiGate
Correct Answer: ACD
Question 4:
Refer to the exhibit.
In the topology shown in the exhibit, both PLCs can communicate directly with each other, without going through the firewall.
Which statement about the topology is true?
A. PLCs use IEEE802.1Q protocol to communicate each other.
B. An administrator can create firewall policies in the switch to secure between PLCs.
C. This integration solution expands VLAN capabilities from Layer 2 to Layer 3.
D. There is no micro-segmentation in this topology.
Correct Answer: D
Question 5:
Which three common breach points can be found in a typical OT environment? (Choose three.)
A. Global hat
B. Hard hat
C. VLAN exploits
D. Black hat
E. RTU exploits
Correct Answer: CDE
Question 6:
An OT network administrator is trying to implement active authentication.
Which two methods should the administrator use to achieve this? (Choose two.)
A. Two-factor authentication on FortiAuthenticator
B. Role-based authentication on FortiNAC
C. FSSO authentication on FortiGate
D. Local authentication on FortiGate
Correct Answer: AB
Question 7:
Refer to the exhibit.

An OT administrator ran a report to identify device inventory in an OT network. Based on the report results, which report was run?
A. A FortiSIEM CMDB report
B. A FortiAnalyzer device report
C. A FortiSIEM incident report
D. A FortiSIEM analytics report
Correct Answer: A
Question 8:
An OT administrator deployed many devices to secure the OT network. However, the SOC team is reporting that there are too many alerts, and that many of the alerts are false positive. The OT administrator would like to find a solution that eliminates repetitive tasks, improves efficiency, saves time, and saves resources.
Which products should the administrator deploy to address these issues and automate most of the manual tasks done by the SOC team?
A. FortiSIEM and FortiManager
B. FortiSandbox and FortiSIEM
C. FortiSOAR and FortiSIEM
D. A syslog server and FortiSIEM
Correct Answer: C
Question 9:
Refer to the exhibit.
You need to configure VPN user access for supervisors at the breach and HQ sites using the same soft FortiToken. Each site has a FortiGate VPN gateway.
What must you do to achieve this objective?
A. You must use a FortiAuthenticator.
B. You must register the same FortiToken on more than one FortiGate.
C. You must use the user self-registration server.
D. You must use a third-party RADIUS OTP server.
Correct Answer: A
Question 10:
An OT supervisor has configured LDAP and FSSO for the authentication. The goal is that all the users be authenticated against passive authentication first and, if passive authentication is not successful, then
users should be challenged with active authentication. What should the OT supervisor do to achieve this on FortiGate?
A. Configure a firewall policy with LDAP users and place it on the top of list of firewall policies.
B. Enable two-factor authentication with FSSO.
C. Configure a firewall policy with FSSO users and place it on the top of list of firewall policies.
D. Under config user settings configure set auth-on-demand implicit.
Correct Answer: D
Question 11:
An OT network architect needs to secure control area zones with a single network access policy to provision devices to any number of different networks.
On which device can this be accomplished?
A. FortiGate
B. FortiEDR
C. FortiSwitch
D. FortiNAC
Correct Answer: D
Question 12:
Refer to the exhibit.

Based on the topology designed by the OT architect, which two statements about implementing OT security are true? (Choose two.)
A. Firewall policies should be configured on FortiGate-3 and FortiGate-4 with industrial protocol sensors.
B. Micro-segmentation can be achieved only by replacing FortiGate-3 and FortiGate-4 with a pair of FortiSwitch devices.
C. IT and OT networks are separated by segmentation.
D. FortiGate-3 and FortiGate-4 devices must be in a transparent mode.
Correct Answer: CD
Question 13:
When you create a user or host profile, which three criteria can you use? (Choose three.)
A. Host or user group memberships
B. Administrative group membership
C. An existing access control policy
D. Location
E. Host or user attributes
Correct Answer: ADE
Question 14:
Refer to the exhibit, which shows a non-protected OT environment.

An administrator needs to implement proper protection on the OT network.
Which three steps should an administrator take to protect the OT network? (Choose three.)
A. Deploy an edge FortiGate between the internet and an OT network as a one-arm sniffer.
B. Deploy a FortiGate device within each ICS network.
C. Configure firewall policies with web filter to protect the different ICS networks.
D. Configure firewall policies with industrial protocol sensors
E. Use segmentation
Correct Answer: ACD
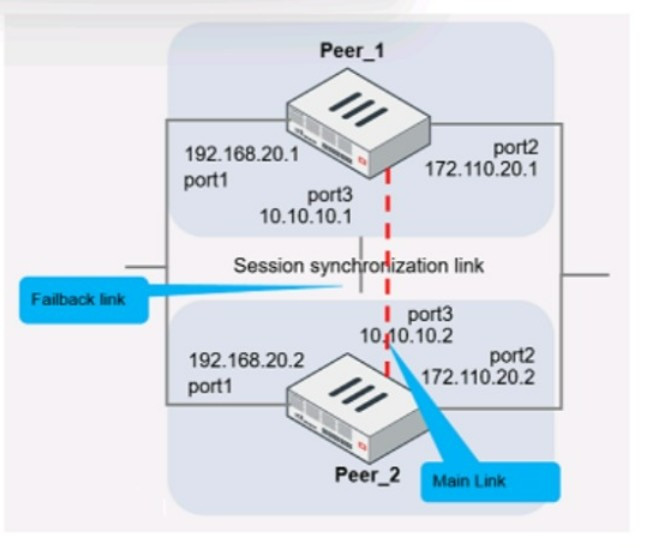
Question 15:
Refer to the exhibit.

Given the configurations on the FortiGate, which statement is true?
A. FortiGate is configured with forward-domains to reduce unnecessary traffic.
B. FortiGate is configured with forward-domains to forward only domain controller traffic.
C. FortiGate is configured with forward-domains to forward only company domain website traffic.
D. FortiGate is configured with forward-domains to filter and drop non-domain controller traffic.
Correct Answer: A
…